Mysterious Elephant: The stealthy cyber espionage campaign targets Bangladesh
In the shadowy corridors of global cyber espionage, a new and increasingly aggressive actor has emerged, one that is not only technically adept but also laser-focused on South Asia’s geopolitical nerve centres.
Dubbed Mysterious Elephant by Kaspersky’s Global Research and Analysis Team (GReAT), this advanced persistent threat (APT) group has been quietly infiltrating government and foreign affairs institutions across the region since at least 2023. And in 2025, its operations have taken a troubling turn, with Bangladesh now among its top targets.
A ghost in the machine: Who is ‘Mysterious Elephant’?
First detected in late 2023, Mysterious Elephant initially appeared to mimic known threat actors like Confucius and SideWinder. But deeper forensic analysis revealed something more complex: a hybrid entity stitching together abandoned code from multiple APTs – Origami Elephant, Confucius, even legacy tools once used by Chinese-linked groups – then refining and repurposing them for its own campaigns.
Unlike many financially motivated cybercriminals, Mysterious Elephant operates with the patience and precision of a state-backed intelligence unit. Its hallmark? Long-term infiltration, minimal digital footprint, and a fixation on diplomatic communications, particularly those flowing through consumer-grade apps like WhatsApp.
Bangladesh in the crosshairs
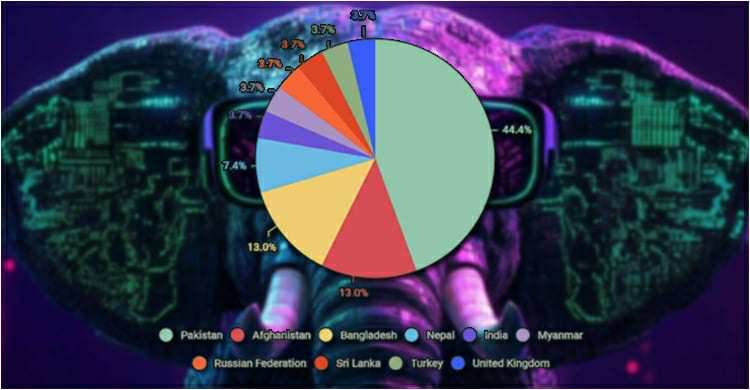
While Pakistan remains the group’s primary focus, evidenced by phishing lures referencing its UN Security Council bid, Bangladesh has surged into the top tier of targeted nations in 2025.
According to GReAT telemetry, Bangladesh now ranks second only to Pakistan in terms of attack volume, with confirmed intrusions detected in foreign ministry networks, diplomatic missions abroad, and strategic policy think tanks.
What makes Bangladesh especially vulnerable? Experts point to a combination of factors: increasing digitalisation of government services, reliance on widely used communication platforms like WhatsApp for official correspondence, and gaps in advanced threat detection capabilities across public-sector IT infrastructure.
“Mysterious Elephant doesn’t just spray-and-pray,” explains Noushin Shabab, senior security researcher at GReAT. “
Weaponising WhatsApp: The silent data heist
Perhaps the most alarming innovation in Mysterious Elephant’s 2025 campaign is its WhatsApp-specific exfiltration toolkit. Recognising that many Bangladeshi officials use WhatsApp Desktop for sharing sensitive documents – often bypassing formal secure channels – the group has engineered malware that automatically hunts, decrypts, and uploads WhatsApp-shared files.
Two key tools stand out:
Stom Exfiltrator: Scans the hidden WhatsApp Desktop transfer directory (%AppData%\Packages\...\LocalState\Shared\transfers\) for documents, images, and archives. It then compresses and Base64-encodes them before shipping them to command-and-control (C2) servers.
ChromeStealer: Targets Google Chrome profiles to steal session cookies and local storage data—potentially granting attackers persistent access to webmail, cloud drives, and even WhatsApp Web sessions.
Custom tools, cloud cover: Evading detection
Mysterious Elephant’s technical sophistication extends beyond data theft. The group now deploys a suite of custom and repurposed open-source tools designed to operate entirely in memory—leaving little trace on disk.
BabShell: A lightweight C++ reverse shell that spawns threads for parallel command execution and logs outputs with timestamped filenames. It triggers persistence via Windows NetworkProfile events—activating only when the device connects to a new network, a tactic that bypasses many static detection rules.
MemLoader HidenDesk & MemLoader Edge: Reflective PE loaders that decrypt and execute payloads like Remcos RAT and VRat directly in RAM. Both include anti-sandbox logic—such as checking for fewer than 40 running processes or attempting to connect to bing.com:445—to stall automated analysis.
The group’s infrastructure is equally elusive. Leveraging wildcard DNS records and rotating virtual private servers (VPS)—with a noted preference for providers in Eastern Europe and Southeast Asia—Mysterious Elephant ensures its C2 domains change faster than defenders can block them.
Why Bangladesh? Geopolitics meets cyber strategy
Analysts believe Mysterious Elephant’s interest in Bangladesh is not random. As a key player in Bay of Bengal regional security, a growing partner in Indo-Pacific initiatives, and a nation navigating complex ties with both China and India, Bangladesh holds strategic intelligence value.
Moreover, Bangladesh’s ongoing digital transformation has expanded its attack surface without always matching it with equivalent cybersecurity investment. Many government offices still rely on outdated software, lack endpoint detection systems, and permit the use of personal devices for official communication—creating fertile ground for spear-phishing.
A call to action
Kaspersky GReAT urges Bangladeshi institutions—especially those in foreign affairs, defence, and strategic policy—to take immediate steps:
Disable WhatsApp Desktop for handling classified or sensitive material; migrate to vetted, end-to-end encrypted government messaging platforms.
Implement application allowlisting and network segmentation to limit lateral movement.
Conduct regular phishing simulations and train staff to spot lures mimicking diplomatic correspondence.
Deploy EDR (Endpoint Detection and Response) solutions capable of detecting in-memory threats like BabShell and MemLoader.
International collaboration is also critical. Given Mysterious Elephant’s regional scope—spanning Pakistan, Sri Lanka, Nepal, and Afghanistan—a coordinated threat-sharing mechanism among South Asian CERTs could help disrupt its operations.
The elephant in the room
Mysterious Elephant may be “mysterious,” but its intent is clear: to silently harvest the digital lifeblood of South Asia’s diplomatic corps. For Bangladesh, a nation increasingly central to regional geopolitics, the stakes couldn’t be higher. In the invisible war of bytes and borders, vigilance isn’t optional—it’s existential.

