Kaspersky traces HackingTeam-linked spyware after years of silence
Kaspersky’s Global Research and Analysis Team (GReAT) has identified a new wave of cyberespionage activity tied to Memento Labs, the successor to the notorious Italian surveillance firm HackingTeam, marking the first public evidence of its operations since HackingTeam’s near-total disappearance from the threat landscape years ago.
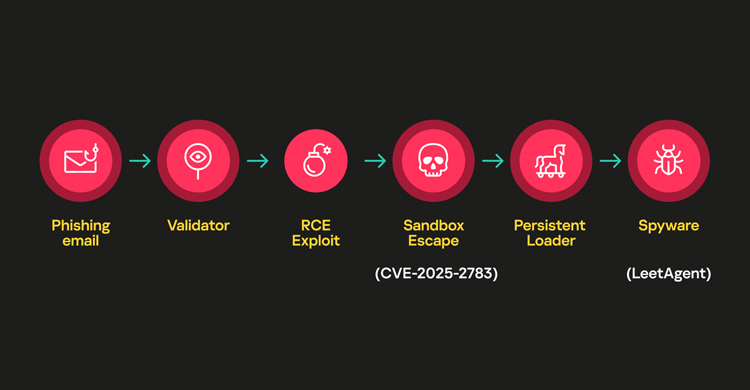
The discovery emerged from an investigation into Operation ForumTroll, an Advanced Persistent Threat (APT) campaign that exploited a zero-day vulnerability in Google Chrome (CVE-2025-2783) through phishing emails targeting Russian-speaking entities. First detected in March 2025, the operation deployed a previously undocumented spyware dubbed LeetAgent, which researchers have now linked to Dante—a sophisticated surveillance platform developed by Memento Labs.
According to Kaspersky, Dante shares core architectural frameworks and code signatures with HackingTeam’s infamous Remote Control System (RCS), confirming a direct lineage between the defunct vendor and its modern incarnation. The spyware employs advanced evasion techniques, including environment checks to avoid analysis in virtual or sandboxed systems.
“Uncovering Dante’s origins was like navigating through hell,” said Boris Larin, Principal Security Researcher at Kaspersky GReAT. “It required peeling back layers of heavily obfuscated code, tracing rare digital fingerprints across years of malware evolution, and connecting them to a corporate shadow trail. Perhaps that’s why they named it Dante.”
Operation ForumTroll has been active since 2022, primarily targeting organisations in Russia and Belarus. Notably, the attackers demonstrate fluent but non-native Russian language proficiency, suggesting possible foreign involvement or outsourcing.
The initial LeetAgent infection was flagged by Kaspersky Next XDR Expert, triggering a deeper forensic investigation that ultimately exposed the Memento Labs connection. The full technical analysis, along with indicators of compromise (IOCs) and ongoing tracking of ForumTroll, is now available to subscribers of Kaspersky’s APT Intelligence Reporting Service via the Threat Intelligence Portal.
A detailed public report has also been published on Securelist.com, Kaspersky’s threat research platform.
Established in 2008, the Global Research & Analysis Team (GReAT) is Kaspersky’s elite cybersecurity unit, with over 35 experts stationed across Europe, Russia, Latin America, Asia, and the Middle East. GReAT specialises in uncovering state-sponsored cyber-espionage campaigns, APTs, ransomware, and emerging cybercriminal trends, driving innovation in global threat intelligence and malware defence.

